Posted in: Sports, TV, WWE | Tagged: hacker, nmap, Smackdown, wwe
Exclusive: Secrets of the WWE Smackdown Hacker Revealed
On yesterday's WWE Friday Night Smackdown on Fox, the mysterious hacker returned once again, interrupting a match with a pre-recorded video message. "We have heard all the lies," the hacker, voice disguised and cloaked in a black hood, said. "But when will we hear the truth?" A video was shown featuring the Jimmy and Jay Uso, Alexa Bliss and Nikki Cross, Miz and Morrison, Sasha Banks and Bayley, and Kofi Kingston and Big E. "Some keep their friends close. Others keep their enemies closer." The words "The truth will be heard" then flashed on the screen.
Who is the hacker? What do they want? What truth do they have to reveal? We don't know the answers to those questions. One suspect, Xavier Woods, denies it's him, saying on Twitter, "A few people keep asking if this is me. If it were me then I would have gone with blue and pink instead of blue and green, there would be a gm mode book someplace, and most importantly there would be a crown somewhere."
WWE Smackdown Hacker's Secrets Revealed
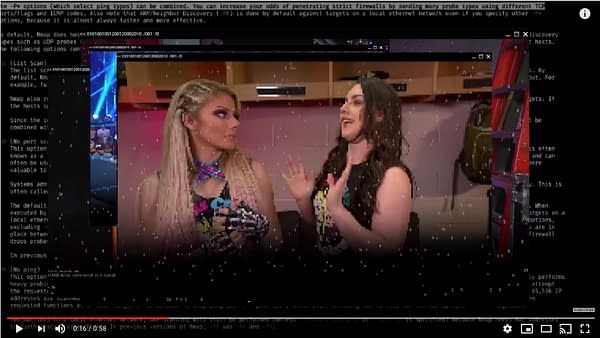
The WWE Hacker has an interesting computer setup. Six monitors in addition to two MacBooks. An unnecessarily large speaker system is right in the middle, and the upper left and right monitors are wasted for some reason just to show the hacker's logo. In contrast, the bottom left screen is used only to show a Matrix screensaver for some reason. On the remaining screens, the Hacker has several full-screen terminals using a 1980s monochrome theme displaying random, scrolling output. This hacker is clearly very sophisticated in the hacking arts, if for no other reason than running multiple external monitors from those MacBooks without causing them to overheat.

But when the WWE Hacker shows their video, we get a clearer look at the screen in the background. There, we can see text that appears to be the man page for the open-source port scanning software nmap. Is the hacker less sophisticated than we thought? Are they making this up as they go along, consulting the instructions for their hacking software as they go? Shouldn't a hacker with an eight-screen computer setup know how to use nmap?!
Here are the instructions the WWE Hacker was using, which can be seen by typing "man nmap" in the terminal of your Linux or Unix based computer if you have the program installed (go ahead and try it).
By default, Nmap does host discovery and then performs a port scan against each host it determines is online. This is true even if you specify non-default host discovery types such as UDP probes
(-PU). Read about the -sn option to learn how to perform only host discovery, or use -Pn to skip host discovery and port scan all target hosts. The following options control host discovery:
-sL (List Scan) .
The list scan is a degenerate form of host discovery that simply lists each host of the network(s) specified, without sending any packets to the target hosts. By default, Nmap still does reverse-DNS resolution on the hosts to learn their names. It is often surprising how much useful information simple hostnames give out. For example, fw.chi is the name of one company's Chicago firewall. Nmap also reports the total number of IP addresses at the end. The list scan is a good sanity check to ensure that you have proper IP addresses for your targets. If the hosts sport domain names you do not recognize, it is worth investigating further to prevent scanning the wrong company's network.
Since the idea is to simply print a list of target hosts, options for higher level functionality such as port scanning, OS detection, or ping scanning cannot be combined with this. If you wish to disable ping scanning while still performing such higher level functionality, read up on the -Pn (skip ping) option.
-sn (No port scan) .
This option tells Nmap not to do a port scan after host discovery, and only print out the available hosts that responded to the host discovery probes. This is often known as a "ping scan", but you can also request that traceroute and NSE host scripts be run. This is by default one step more intrusive than the list scan, and can often be used for the same purposes. It allows light reconnaissance of a target network without attracting much attention. Knowing how many hosts are up is more valuable to attackers than the list provided by list scan of every single IP and host name.
Systems administrators often find this option valuable as well. It can easily be used to count available machines on a network or monitor server availability. This is often called a ping sweep, and is more reliable than pinging the broadcast address because many hosts do not reply to broadcast queries.
The default host discovery done with -sn consists of an ICMP echo request, TCP SYN to port 443, TCP ACK to port 80, and an ICMP timestamp request by default. When executed by an unprivileged user, only SYN packets are sent (using a connect call) to ports 80 and 443 on the target. When a privileged user tries to scan targets on a local ethernet network, ARP requests are used unless –send-ip was specified. The -sn option can be combined with any of the discovery probe types (the -P* options, excluding -Pn) for greater flexibility. If any of those probe type and port number options are used, the default probes are overridden. When strict firewalls are in place between the source host running Nmap and the target network, using those advanced techniques is recommended. Otherwise hosts could be missed when the firewall drops probes or their responses. In previous releases of Nmap, -sn was known as -sP..
-Pn (No ping) .
This option skips the Nmap discovery stage altogether. Normally, Nmap uses this stage to determine active machines for heavier scanning. By default, Nmap only performs heavy probing such as port scans, version detection, or OS detection against hosts that are found to be up. Disabling host discovery with -Pn causes Nmap to attempt the requested scanning functions against every target IP address specified. So if a class B target address space (/16) is specified on the command line, all 65,536 IP addresses are scanned. Proper host discovery is skipped as with the list scan, but instead of stopping and printing the target list, Nmap continues to perform requested functions as if each target IP is active. To skip ping scan and port scan, while still allowing NSE to run, use the two options -Pn -sn together.
For machines on a local ethernet network, ARP scanning will still be performed (unless –disable-arp-ping or –send-ip is specified) because Nmap needs MAC addresses to further scan target hosts. In previous versions of Nmap, -Pn was -P0. and -PN..
Did you read all of that? Good. Now you're as smart as the WWE hacker! Oh, damn, we probably shouldn't have revealed this critical information. Or maybe that's what we want you to think. Maybe we know all this about the Hacker because the Hacker is us, and we're just trying to throw you off the trail! Food for thought.